1. A Remote Access Trojan (RAT) is malware program thatgive an intruder administractive control over a target computer.RATS are usually downloaded invisibly with a-user-requested program such as game or sent as an email attachment.Once the host system is compromise,the intruder may use it to distribute more RAT for botnet
2. A keylogger is hardware device or small program that monitor each keystroke a user types on a specific computer's keyboard.As a hardware device,a keylogger is a small baterry sized plug that servers as a connector between the user's keyboard and computer
3. On the internet,distributed denial of service(DdoS) attack is one in which a multitude of compromise system attack a single target,thereby causing a denial of service for users of the targeted system
4.A denial of service(Dos)attack is a malicious attempt to make a server or network resource unavailable to users ,usually by temporarily interrupting or suspending the service of a host connected to the internet.
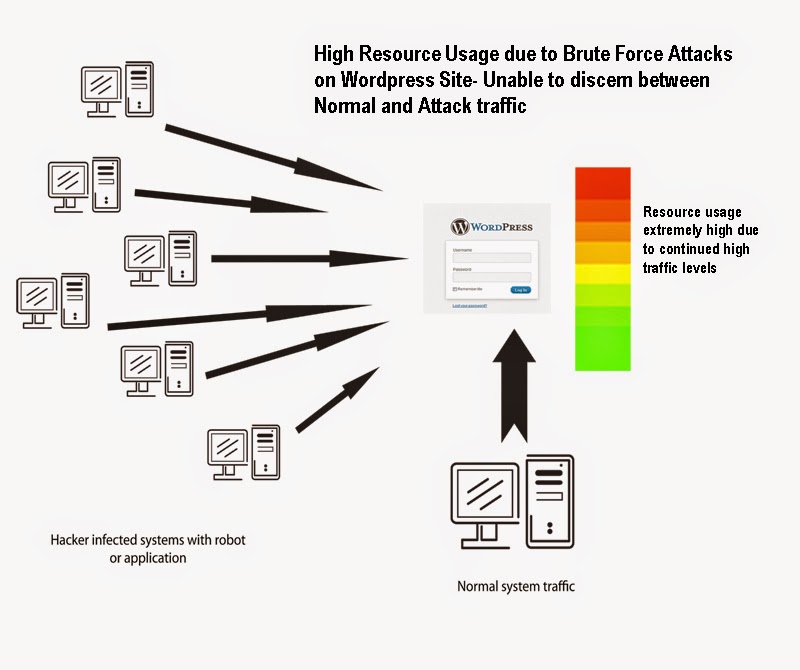
5.A brute force is a trial and error method to use information such as password and personal identification number (PIN).In brute force attack,automated software is used to generate a large number of consecutive guesses as to as the value of the desired data.Brute force attack may be used by criminal to cracked encrypted data,or by security analyst to test an organizations network security.
6 Sniffing is the technique that is used for intercepting took this or steal or diffrent data traffic on a network.For example,there are 3 computers connected together via a single link.When computer A to computer B intercouse,then the pull of this technique is the computer C (sniffer) that are in the network can participate listen to and record all activities performed by the computer A and computer B.Computer C would then pretend be computer B to A.thus,if lucky then the password to enter or access of both system can get easily.
7. A botnet is a collection of internet connected program communicating with other similar program in order to perform task.This can be as mudane as keeping control of Internet Relay Chat (IRC) channel,or it could be used to send spam email or participate in distribute of denial of service attacks
8.Website defacement is attack on a website that change the visual appereance of the website or web page.This is typically of the work of the system crackers,who break into a system server and replace the hosted website of one of their own.Defacement is generally meant of the kind of electronic grafiti,althought recently it has become a means to spread messages by politically motivate "cyber protesters" or hacktivits.
9.Phishing is an email fraud in which perpetrator send out legitimate looking email in an attempt to gather personal and financial information from recipients.
10.Worm is self replication viruses that does not alter file but resides in active memory and duplicate itself.
11. Hijacking is a type of network security attack in which the attacker takes control of the communication-just an airplane hijacker takes control of the flight-between two entities and masquerades one of them.
12.Sql injection is a type of security exploit in which the attacker adds Structured Query Language (Sql) code to a web form input box to gain access to resources or make change to data.
Source:http://searchsecurity.techtarget.com/










.gif)
