Sunday, April 5, 2015
Conclusion
As a conclusion,not every computer in this world is safe.Computer will always exposed to any kind of threat or attack.An attack usually is perpetrated by someone with bad intentions ,like Black hatted attacks falls in this category.These people will do anything to hack into your personal information in your computer.Computer users should install security software to prevent any kind of network attack such as antivirus.So,we should install security software in order to avoid the threat of network attack.
Saturday, April 4, 2015
Symptom Of Network Attack
An infected computer has one or more of the following symptom:
1. Operating System run much slower than usual.
2. Avaible memory is less than expected.
3. File become corrupted.
4. Screen display unsual message or image.
5. Music or unusual sound play randomly
6. Existing program and file disappear.
7. Program or file do not work properly.
8. Unknown program or files mysteriously appear
.
9. System property change.
10. Operating System does not start up.
11. Operating System shut down unexpectedly.
1. Operating System run much slower than usual.
2. Avaible memory is less than expected.
3. File become corrupted.
4. Screen display unsual message or image.
5. Music or unusual sound play randomly
6. Existing program and file disappear.
7. Program or file do not work properly.
8. Unknown program or files mysteriously appear
.
9. System property change.
10. Operating System does not start up.
11. Operating System shut down unexpectedly.
Friday, April 3, 2015
Software to prevent viruses
Tips for preventing viruses and other malware.
1. Never start a computer with removeable media inserted in the drives or plugged in the port,unless the media are uninfected.
2.Never open an e-mail attachment unless you are expecting it and it is from trusted source.
3. Set the macro security in the program so that you can enable or disable macros.Enable macros only if the document is from a trusted source and you are expecting it.
4. Install an antivirus program on all of your computer.Update the software and the virus signature files regularly.
5. Scan all download program for virus or other malware.
6. If the antivirus program flags an e-mail attachment as infected,delete or quarantine the attacment immediately.
7. Before using any removeable media,Scan the media for malware.Follow this procedure even for shrink-wrapped software from major developers.Some commercial software has been infected and distributing to unsuspecting users.
8. Install a firewall program.
9. Stay informed about new virus alert and virus hoaxes.
1. Never start a computer with removeable media inserted in the drives or plugged in the port,unless the media are uninfected.
2.Never open an e-mail attachment unless you are expecting it and it is from trusted source.
3. Set the macro security in the program so that you can enable or disable macros.Enable macros only if the document is from a trusted source and you are expecting it.
4. Install an antivirus program on all of your computer.Update the software and the virus signature files regularly.
5. Scan all download program for virus or other malware.
6. If the antivirus program flags an e-mail attachment as infected,delete or quarantine the attacment immediately.
7. Before using any removeable media,Scan the media for malware.Follow this procedure even for shrink-wrapped software from major developers.Some commercial software has been infected and distributing to unsuspecting users.
8. Install a firewall program.
9. Stay informed about new virus alert and virus hoaxes.
video source:https://www.youtube.com/watch?v=CiIToBYDtqA
History of Internet and Network attack
Today the dominant basis for data communications worldwide was a new
concept at the time of the conception of the ARPANET. Prior to the
advent of packet switching, both voice and data communications had been
based on the idea of circuit switching,
as in the traditional telephone circuit, wherein each telephone call is
allocated a dedicated, end to end, electronic connection between the
two communicating stations. Such stations might be telephones or
computers. The (temporarily) dedicated line is typically composed of
many intermediary lines which are assembled into a chain that stretches
all the way from the originating station to the destination station.
With packet switching, a data system could use a single communication
link to communicate with more than one machine by collecting data into datagrams and transmitting these as packets onto the attached network link, as soon as the link becomes idle. Thus, not only can the link be shared, much as a single post box can be used to post letters to different destinations, but each packet can be routed independently of other packets.
The earliest ideas for a computer network intended to allow general communications among computer users were formulated by computer scientist J. C. R. Licklider of Bolt, Beranek and Newman (BBN), in April 1963, in memoranda discussing the concept of the "Intergalactic Computer Network". Those ideas encompassed many of the features of the contemporary Internet. In October 1963, Licklider was appointed head of the Behavioral Sciences and Command and Control programs at the Defense Department's Advanced Research Projects Agency (ARPA). He convinced Ivan Sutherland and Bob Taylor that this network concept was very important and merited development, although Licklider left ARPA before any contracts were assigned for development.
Sutherland and Taylor continued their interest in creating the network, in part, to allow ARPA-sponsored researchers at various corporate and academic locales to utilize computer provide by ARPA, and, in part, to quickly distribute new software and other computer science results. Taylor had three computer terminals in his office, each connected to separate computers, which ARPA was funding: one for the System Development Corporation (SDC) Q-32 in Santa Monica, one for Project Genie at the University of California, Berkeley, and another for Multics at the Massachusetts Institute of Technology. . That idea is the ARPANET.
Meanwhile, since the early 1960s, Paul Baran at the RAND Corporation had been researching systems that could survive nuclear war and presented in the United Kingdom National Physical Laboratory (NPL) the first public demonstration of packet switching on 5 August 1968.
Source:wikipedia
The earliest ideas for a computer network intended to allow general communications among computer users were formulated by computer scientist J. C. R. Licklider of Bolt, Beranek and Newman (BBN), in April 1963, in memoranda discussing the concept of the "Intergalactic Computer Network". Those ideas encompassed many of the features of the contemporary Internet. In October 1963, Licklider was appointed head of the Behavioral Sciences and Command and Control programs at the Defense Department's Advanced Research Projects Agency (ARPA). He convinced Ivan Sutherland and Bob Taylor that this network concept was very important and merited development, although Licklider left ARPA before any contracts were assigned for development.
Sutherland and Taylor continued their interest in creating the network, in part, to allow ARPA-sponsored researchers at various corporate and academic locales to utilize computer provide by ARPA, and, in part, to quickly distribute new software and other computer science results. Taylor had three computer terminals in his office, each connected to separate computers, which ARPA was funding: one for the System Development Corporation (SDC) Q-32 in Santa Monica, one for Project Genie at the University of California, Berkeley, and another for Multics at the Massachusetts Institute of Technology. . That idea is the ARPANET.
Meanwhile, since the early 1960s, Paul Baran at the RAND Corporation had been researching systems that could survive nuclear war and presented in the United Kingdom National Physical Laboratory (NPL) the first public demonstration of packet switching on 5 August 1968.
Source:wikipedia
Thursday, April 2, 2015
Advantage and disadvantage of network attack
What is hacking?
Hacking is the practice of modifying the features of a system, in order to accomplish a goal outside of the creator's original purpose. The person who is consistently engaging in hacking activities, and has accepted hacking as a lifestyle and philosophy of their choice, is called a hacker.
Advantages of hacking
-Can be used to recover lost information where the computer password has been lost.
-Teaches u that no technology is 100% secure
-To test how good security is on your own network. ;) -Teaches u that no technology is 100% secure
They call it white hat computer hacking.
-hacking is good with games especially when you are online but the only problem is
if the gaming server finds out that you have been hacking then you could get chucked off the gaming server so watch out
if the gaming server finds out that you have been hacking then you could get chucked off the gaming server so watch out
Disadvantages of hacking
-Criminals can use it to their advantage.
-It can harm someone's privacy
-It can harm someone's privacy
-It's Illegal.
-It destroys other works
source:http://tissans.blogspot.com/2011/11/define-hacking-advantages-and.html
source:http://tissans.blogspot.com/2011/11/define-hacking-advantages-and.html
Network Security
NETWORK SECURITY
The easiest way to protect a network from an outside
attack is to close it off completely from the outside world. A closed network
provides connectivity only to trusted known parties and sites; a closed network
does not allow a connection to public networks.
There is a estimates that 60 to 80 percent of network misuse
comes from inside the enterprise where the misuse has taken place.
With the development of large open networks, security
threats have increased significantly in the past 20 years. Hackers have discovered
more network vulnerabilities, and because you can now download applications
that require little or no hacking knowledge to implement, applications intended
for troubleshooting and maintaining and optimizing networks can, in the wrong
hands, be used maliciously and pose severe threats.
Types of attack:
Classes of attack might include passive monitoring of
communications, active network attacks, close-in attacks, exploitation by
insiders, and attacks through the service provider. Information systems and
networks offer attractive targets and should be resistant to attack from the
full range of threat agents, from hackers to nation-states. A system must be
able to limit damage and recover rapidly when attacks occur.
There are five types of attack:
There are five types of attack:
Passive Attack
A passive attack monitors unencrypted
traffic and looks for clear-text passwords and sensitive information that can
be used in other types of attacks. Passive attacks include
traffic analysis, monitoring of unprotected communications, decrypting weakly
encrypted traffic, and capturing authentication information such as passwords.
Passive interception of network operations enables adversaries to see upcoming
actions. Passive attacks result in the disclosure of information or data files
to an attacker without the consent or knowledge of the user
.
Active Attack
In an active attack, the attacker tries to
bypass or break into secured systems. This can be done through stealth,
viruses, worms, or Trojan horses. Active attacks include attempts to circumvent
or break protection features, to introduce malicious code, and to steal or
modify information. These attacks are mounted against a network backbone,
exploit information in transit, electronically penetrate an enclave, or attack
an authorized remote user during an attempt to connect to an enclave. Active
attacks result in the disclosure or dissemination of data files, DoS, or
modification of data.
Distributed Attack
A distributed attack requires that the
adversary introduce code, such as a Trojan horse or back-door program, to a
“trusted” component or software that will later be distributed to many other
companies and users Distribution attacks focus on the malicious modification of
hardware or software at the factory or during distribution. These attacks
introduce malicious code such as a back door to a product to gain unauthorized
access to information or to a system function at a later date.
Insider Attack
An insider attack involves someone from the
inside, such as a disgruntled employee, attacking the network Insider attacks
can be malicious or no malicious. Malicious insiders intentionally eavesdrop,
steal, or damage information; use information in a fraudulent manner; or deny
access to other authorized users. No malicious attacks typically result from
carelessness, lack of knowledge, or intentional circumvention of security for
such reasons as performing a task
NETWORK SECURITY RECONNAISSANCE ATTACK
A reconnaissance attack occurs when an adversary tries to
learn information about your network
Reconnaissance is the unauthorized discovery and mapping of systems, services, or vulnerabilities.
Reconnaissance is also known as information gathering and, in most cases, precedes an actual access or DoS attack. First, the malicious intruder typically conducts a ping sweep of the target network to determine which IP addresses are alive. Then the intruder determines which services or ports are active on the live IP addresses. From this information, the intruder queries the ports to determine the type and version of the application and operating system running on the target host.
Reconnaissance is the unauthorized discovery and mapping of systems, services, or vulnerabilities.
Reconnaissance is also known as information gathering and, in most cases, precedes an actual access or DoS attack. First, the malicious intruder typically conducts a ping sweep of the target network to determine which IP addresses are alive. Then the intruder determines which services or ports are active on the live IP addresses. From this information, the intruder queries the ports to determine the type and version of the application and operating system running on the target host.
Reconnaissance is somewhat analogous to a thief
investigating a neighborhood for vulnerable homes, such as an unoccupied
residence or a house with an easy-to-open door or window. In many cases,
intruders look for vulnerable services that they can exploit later when less
likelihood that anyone is looking exists.
Wednesday, April 1, 2015
How that work!
1. A Remote Access Trojan (RAT) is malware program thatgive an intruder administractive control over a target computer.RATS are usually downloaded invisibly with a-user-requested program such as game or sent as an email attachment.Once the host system is compromise,the intruder may use it to distribute more RAT for botnet
2. A keylogger is hardware device or small program that monitor each keystroke a user types on a specific computer's keyboard.As a hardware device,a keylogger is a small baterry sized plug that servers as a connector between the user's keyboard and computer
3. On the internet,distributed denial of service(DdoS) attack is one in which a multitude of compromise system attack a single target,thereby causing a denial of service for users of the targeted system
4.A denial of service(Dos)attack is a malicious attempt to make a server or network resource unavailable to users ,usually by temporarily interrupting or suspending the service of a host connected to the internet.
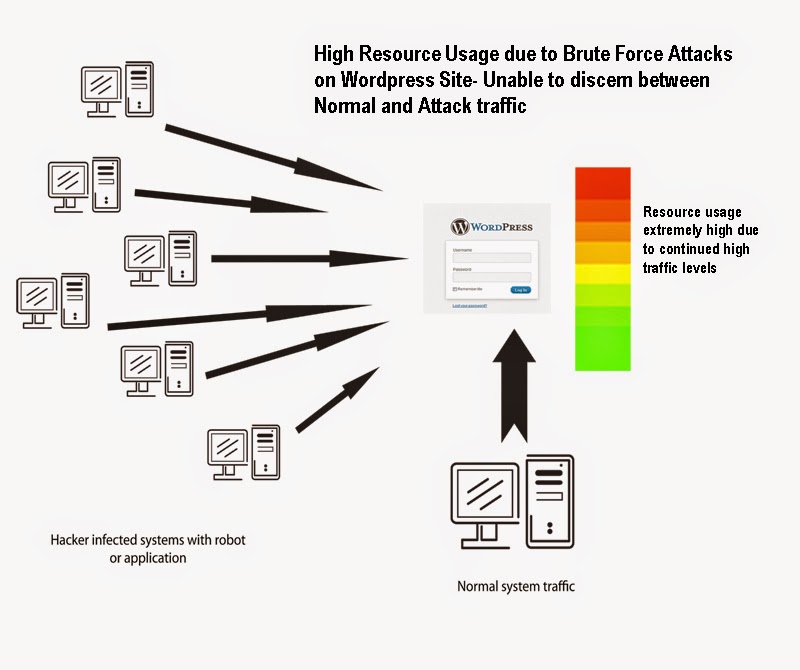
5.A brute force is a trial and error method to use information such as password and personal identification number (PIN).In brute force attack,automated software is used to generate a large number of consecutive guesses as to as the value of the desired data.Brute force attack may be used by criminal to cracked encrypted data,or by security analyst to test an organizations network security.
6 Sniffing is the technique that is used for intercepting took this or steal or diffrent data traffic on a network.For example,there are 3 computers connected together via a single link.When computer A to computer B intercouse,then the pull of this technique is the computer C (sniffer) that are in the network can participate listen to and record all activities performed by the computer A and computer B.Computer C would then pretend be computer B to A.thus,if lucky then the password to enter or access of both system can get easily.
7. A botnet is a collection of internet connected program communicating with other similar program in order to perform task.This can be as mudane as keeping control of Internet Relay Chat (IRC) channel,or it could be used to send spam email or participate in distribute of denial of service attacks
8.Website defacement is attack on a website that change the visual appereance of the website or web page.This is typically of the work of the system crackers,who break into a system server and replace the hosted website of one of their own.Defacement is generally meant of the kind of electronic grafiti,althought recently it has become a means to spread messages by politically motivate "cyber protesters" or hacktivits.
9.Phishing is an email fraud in which perpetrator send out legitimate looking email in an attempt to gather personal and financial information from recipients.
10.Worm is self replication viruses that does not alter file but resides in active memory and duplicate itself.
11. Hijacking is a type of network security attack in which the attacker takes control of the communication-just an airplane hijacker takes control of the flight-between two entities and masquerades one of them.
12.Sql injection is a type of security exploit in which the attacker adds Structured Query Language (Sql) code to a web form input box to gain access to resources or make change to data.
Source:http://searchsecurity.techtarget.com/
2. A keylogger is hardware device or small program that monitor each keystroke a user types on a specific computer's keyboard.As a hardware device,a keylogger is a small baterry sized plug that servers as a connector between the user's keyboard and computer
3. On the internet,distributed denial of service(DdoS) attack is one in which a multitude of compromise system attack a single target,thereby causing a denial of service for users of the targeted system
4.A denial of service(Dos)attack is a malicious attempt to make a server or network resource unavailable to users ,usually by temporarily interrupting or suspending the service of a host connected to the internet.
5.A brute force is a trial and error method to use information such as password and personal identification number (PIN).In brute force attack,automated software is used to generate a large number of consecutive guesses as to as the value of the desired data.Brute force attack may be used by criminal to cracked encrypted data,or by security analyst to test an organizations network security.
6 Sniffing is the technique that is used for intercepting took this or steal or diffrent data traffic on a network.For example,there are 3 computers connected together via a single link.When computer A to computer B intercouse,then the pull of this technique is the computer C (sniffer) that are in the network can participate listen to and record all activities performed by the computer A and computer B.Computer C would then pretend be computer B to A.thus,if lucky then the password to enter or access of both system can get easily.
7. A botnet is a collection of internet connected program communicating with other similar program in order to perform task.This can be as mudane as keeping control of Internet Relay Chat (IRC) channel,or it could be used to send spam email or participate in distribute of denial of service attacks
8.Website defacement is attack on a website that change the visual appereance of the website or web page.This is typically of the work of the system crackers,who break into a system server and replace the hosted website of one of their own.Defacement is generally meant of the kind of electronic grafiti,althought recently it has become a means to spread messages by politically motivate "cyber protesters" or hacktivits.
9.Phishing is an email fraud in which perpetrator send out legitimate looking email in an attempt to gather personal and financial information from recipients.
10.Worm is self replication viruses that does not alter file but resides in active memory and duplicate itself.
11. Hijacking is a type of network security attack in which the attacker takes control of the communication-just an airplane hijacker takes control of the flight-between two entities and masquerades one of them.
12.Sql injection is a type of security exploit in which the attacker adds Structured Query Language (Sql) code to a web form input box to gain access to resources or make change to data.
Source:http://searchsecurity.techtarget.com/
Subscribe to:
Posts (Atom)










.gif)
